When a user tries to access a website, the browser sends Host Header to inform which address the user wants to visit. Just like other headers, attackers can temper Host Header to manipulate how the application works. In this post, I will explain a way to prevent this kind of a Host Header attack.
Scenario
In a nutshell, here is how this attack occurs:
- Attacker changes Host Header (Example: malicious-site.com)
- Attacker makes a request to visit this site
- The web server receives this Host Header (malicious-site.com)
- If the application is using this Host Header to build a link, the attacker’s site will appear in this link. For example, the application may call a JavaScript file with Host Header string in the URL. In this case, the website will call an address such as:
<script src="http://malicious-site.com/script.js"> - Since the website called attacker’s JavaScript, the attacker can do plenty of “bad things”
This type of attack can affect password reset forms and X-Forwarded-Host header as well. For more information about Host Header Attack, visit Reference 1, Reference 2, Reference 3, and Reference 4.
Host Header Vulnerability
Your security scan tool may flag Host Header related findings as a vulnerability. In my case, I had this report from the Cisco vulnerability scan:
Cisco observed that the application is not validating the host header on the following endpoints:
https://domain.com/folder1/page1.aspx
https://domain.com/folder2/page2.aspxIn the absence of host header validation, certain implementations can lead to cache poisoning attacks, allowing attackers to potentially compromise sensitive data. Please also refer to the “Insufficient Cache Control Headers” finding
Have you received a warning about usage of HTTP TRACK or TRACE headers in your web server? Check this post out for more information: How to disable HTTP TRACK and TRACE verbs in IIS?
How to Prevent Host Header Attacks?
There are a couple of best practices for preventing attackers using Host Header to manipulate your application:
- Do not use Host Header in your application code
- If you have to use it, validate it in every page
- Make sure all of your IIS websites have a hostname
- Disable support for X-Forwarded-Host header
How to Fix Host Header Vulnerability?
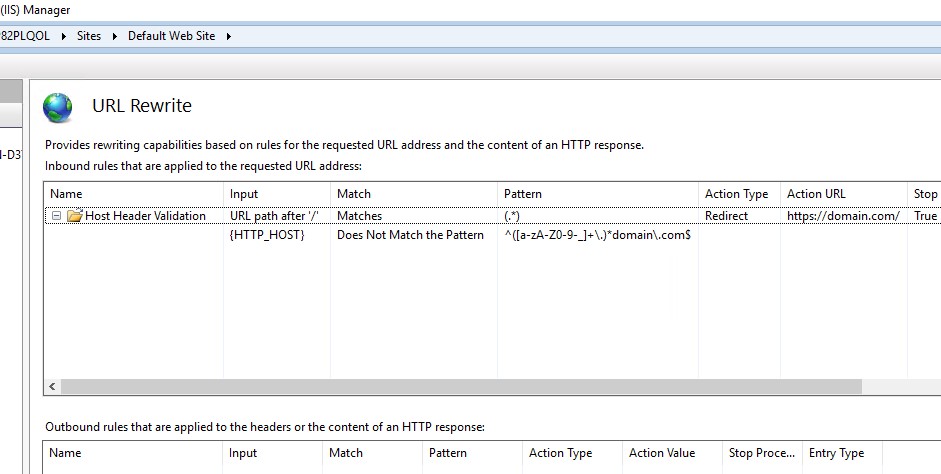
You can use URL Rewrite rules in IIS to find malicious host headers. Perform the steps below:
- Go to IIS Manager
- Click on the site
- Double click on “URL Rewrite” (it should be installed)
- Click “Add Rule(s)” on the right side
- Select “Blank rule”. Click “OK”
- Give a name to the rule
- In “Match URL” section, enter (.) in “Pattern” field
- In “Conditions” section, click “Add”
- Enter {HTTP_HOST} into “Condition input” field
- Select “Does Not Match the Pattern” option from “Check if input string” list
- Enter ^([a-zA-Z0-9-_]+.)domain.com$ into “Pattern” field (change domain to your actual domain)
- In the “Action” section, select “Redirect” from the “Action type” list
- Enter your domain address (https://domain.com/) in the “Redirect URL” field
- Select “Permanent (301)” from the “Redirect type” list
- Click “Apply” on the right side
In addition to the Host Header vulnerability, your security scan tool may flag “Disclosure of private IP address” finding as well. Check this post out to find out the steps to mitigate it: Do not disclose private IP addresses and routing information to unauthorized parties

Hi,
Thank you, I have implemented it and it works. But if the HTTP Request doesn’t contain Host header, the rule still running. How to handle that?
The rule is not supposed to be peformed in that scenario! Can you please collect a Failed Tracing Request log and see if the rule is running? If it is running, is the condition matching?
Hi,
Does it also work when i’m running my website with IP ?
Example : https://198.176.100.200/chatapp/login/login
I’ve never tried with IP but it should work. Make sure to enter IP instead of domain in Step 11