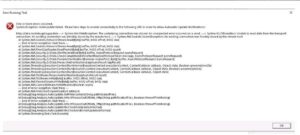
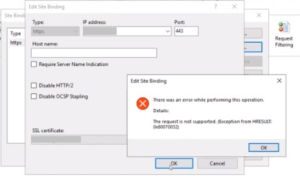
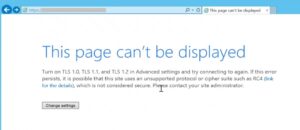
For TLS communication to be successful, a client machine makes a request to IIS server over TLS by sending Client Hello package first. Then the server is supposed to respond it with Server Hello package. What if the server is not sending Server Hello package?
Windows Server
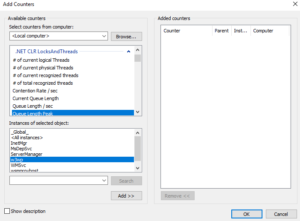
w3wp service is missing for counters in Performance Monitor
Performance Monitor is an easy-to-use tool to record and monitor performance metrics. If you would like to measure IIS performance, you will need to add w3wp as an instance to your counter. What if there is no w3wp instance in the list?
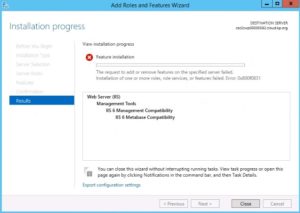
(Solved) Installation of one or more roles or features failed. Error 0x800f0831
Windows Server makes it easier to extend the server capabilities by installing new roles and features. You can use Server Manager to install or uninstall new capabilities. Server Manager provides an easy-to-use wizard to guide you through the process. However, you may come across to this error code in some cases: 0x800f0831.
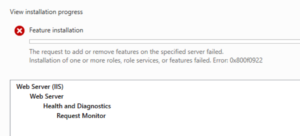
0x800f0922 Update IIS-RequestMonitor of package IIS-WebServer-Core-Package failed
IIS has several features such as WebSocket Protocol, Tracing or Request Monitor that you can install when you need these additional capabilities. You can install them by using Server Manager (That where I run into 0x800f0922 error).
2 Easy Ways to List Programs Installed in Windows
We make our Windows more productive by installing several software. In certain cases such as migrating to a new computer or server, you may need to list programs installed for comparison.