MachineKeys folder stores certificate keys that are used by IIS and Internet Explorer. Because of a permission or application code related issue, this folder may fill up with thousands of files in a short time.
The permanent solution is to correct permissions or fix the code so that the certificate keys in this folder are automatically removed. However, if the permanent fix is taking long time, you will need a practical way of removing old files from this folder.
Steps to clean up MachineKeys folder
Take a backup
Back up the three files below. These files are used by IIS. It’s important to back them up before removing any files from MachinkeKeys folder.
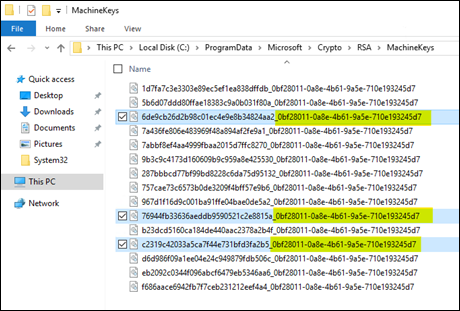
| 6de9cb26d2b98c01ec4e9e8b34824aa2_GUID | iisConfigurationKey |
| d6d986f09a1ee04e24c949879fdb506c_GUID | NetFrameworkConfigurationKey |
| 76944fb33636aeddb9590521c2e8815a_GUID | iisWasKey |
GUID is the MachineGuid. You can find this value in this registry key:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MachineGuid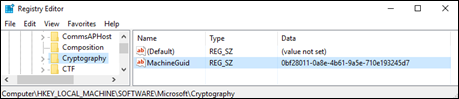
Here are the files to backup from my test machine:
Note 1: If there are millions of files in this folder, File Explorer may not be able to list the content of this folder. Command Prompt may fail searching for files as well. In this case, use the PowerShell command below to search for IIS machine keys:
Get-ChildItem "C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys" -Filter "*c2319c42033a5ca7f44e731bfd3fa2b5*"Once you locate the file, use the command below to copy it to a backup folder:
xcopy C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys\c2319c42033a5ca7f44e731bfd3fa2b5_0bf28011-0a8e-4b61-9a5e-710e193245d7 c:\backup /hNote 2: If II6 Compatibility module is not installed for IIS, the machine key file starting with “c2319c42033a5ca7f44e731bfd3fa2b5” may not exist. Follow the steps above for the other two files.
Remove old files
Run the following command in Command Prompt to remove files older than 90 days in the MachineKeys folder (Make sure to open Command Prompt as Administrator).
ForFiles /p "C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys" /s /d -90 /c "cmd /c del @file /F /A:S"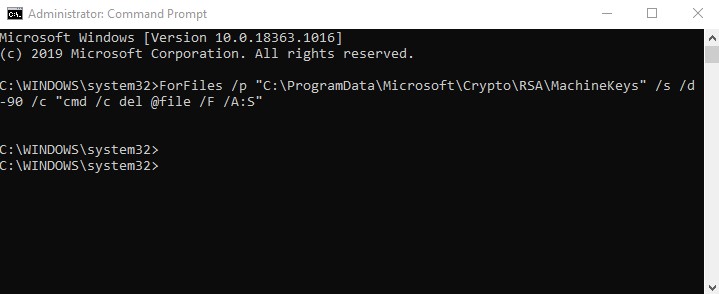
If none of the methods above works because there are just too many files in the folder:
- Create a new folder named MachineKeys1
- Copy IIS key files to this folder
- Remove the original MachineKeys folder
- Rename MachineKeys1 folder to MachineKeys
- Check the permissions of the new folder (Reference)
Why is MachineKeys older filling up?
There are four common reasons why the files in the MachineKeys folder are not automatically removed:
- There is a permission issue that is preventing OS to remove files from that folder. Compare the folder permissions with the ones listed in this document
- There is a code related issue. The application is not removing X.509 certificates once it uses them for communication. More details
- A security software might be performing SSL check and causing these files to persist. Try disabling this software
- Enterprise CA might be failing to respond the request. Check Event Viewer logs for the failed requests
If a file in MachineKeys is corrupted, check this post for solution: Service-specific error code -2146893818 (Event 7024 Invalid Signature)
When there is a permission issue on MachineKeys folder, you may run into Schannel errors as well. Here are the step-by-step instructions to solve Schannel 10013 error: Schannel – The internal error state is 10013

Hello. I was looking for an answer to another question. i have a server 2012 r2 used as terminal server. there are user folders with millions of files in this crypto folder, some very old, is it safe to delete the oldest ones?
Thank you very much for this.
Is there a reason to not skip the command-line option and just do the simpler set of steps you also provided:
“If none of the methods above works because there are just too many files in the folder:
Create a new folder named MachineKeys1
Copy IIS key files to this folder
Remove the original MachineKeys folder
Rename MachineKeys1 folder to MachineKeys
Check the permissions of the new folder (Reference) “
Also, can you provide more information about “The permanent solution is to correct permissions or fix the code so that the certificate keys in this folder are automatically removed.”
Which I think is also the last step of the alternative method of backing-up/deleting the MachineKeys file: “Check the permissions of the new folder (Reference)“.
Thank you again.