When you try to retrieve a connection string from Azure Key Vault, you may come across “DefaultAzureCredential failed to retrieve a token from the included credentials” error.
Detailed error message:
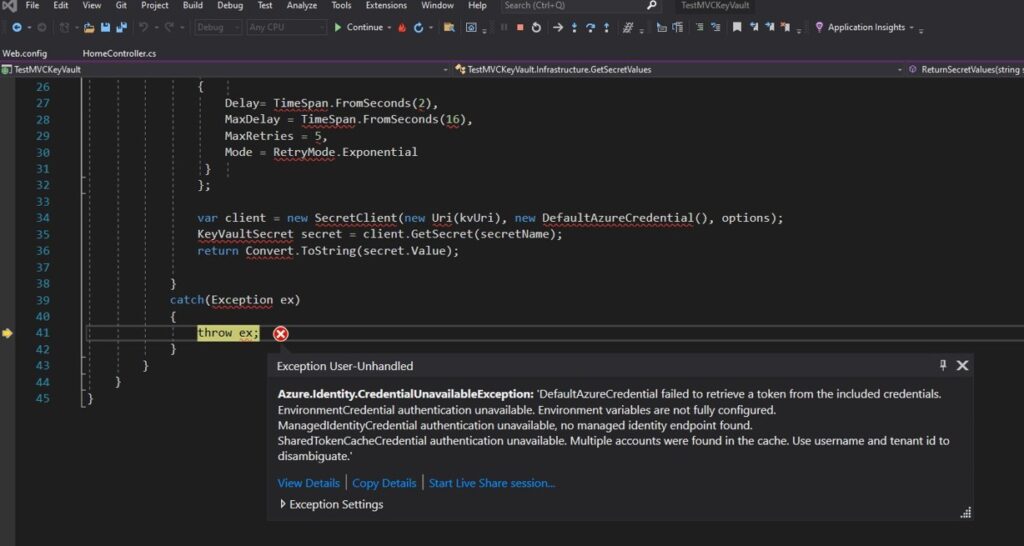
DefaultAzureCredential failed to retrieve a token from the included credentials.
EnvironmentCredential authentication unavailable. Environment variables are not fully configured.
ManagedIdentityCredential authentication unavailable, no Managed Identity endpoint found.
Visual Studio Token provider can’t be accessed at .IdentityService\AzureServiceAuth\tokenprovider.json.
Stored credentials not found.
Need to authenticate user in VSCode Azure Account. Azure CLI not installed.
PowerShell is not installed
This message may show up in the error as well: “SharedTokenCacheCredential authentication unavailable. Multiple accounts were found in the cache. Use username and tenant id to disambiguate”
Solution for ” DefaultAzureCredential failed to retrieve a token” error
In order to solve this issue in a local machine:
- Add Active Directory app registration
- Create access policy for this app registration in Key Vault settings
- Create environment variables for AZURE_CLIENT_ID, AZURE_CLIENT_SECRET, and AZURE_TENANT_ID (Reference)
For connecting an Azure VM to Key Vault, follow this tutorial. Basically, you will need to enable a managed identity for the VM and assign permissions to the identity.
As this page mentions, the way Azure VM connects to Key Vault is slightly different:
Note: DefaultAzureCredential is intended to simplify getting started with the SDK by handling common scenarios with reasonable default behaviors. Developers who want more control or whose scenario isn’t served by the default settings should use other credential types.
If the application is deployed to an Azure host with Managed Identity enabled, the DefaultAzureCredential will authenticate with that account.
Note: We run into an issue with GlobalLogon authentication (unrelated to Azure VM, KeyVault, or other Microsoft products). We had to solve this third-party issue first before getting Azure VM and Key Vault connection work.
Code reference
I created the sample code below to connect Azure Key Vault and retrieve the value of a secret called “testSecret”.
GetSecretValues.cs
using Azure.Core;
using Azure.Identity;
using Azure.Security.KeyVault.Secrets;
using System;
using System.Collections.Generic;
using System.Configuration;
using System.Linq;
using System.Web;
namespace TestMVCKeyVault.Infrastructure
{
public class GetSecretValues
{
public static string ReturnSecretValues(string secretName)
{
try
{
secretName = "testSecret";
var kvUri = Convert.ToString(ConfigurationManager.AppSettings["VaultURI"]);
SecretClientOptions options = new SecretClientOptions()
{
Retry =
{
Delay= TimeSpan.FromSeconds(2),
MaxDelay = TimeSpan.FromSeconds(16),
MaxRetries = 5,
Mode = RetryMode.Exponential
}
};
var client = new SecretClient(new Uri(kvUri), new DefaultAzureCredential(), options);
KeyVaultSecret secret = client.GetSecret(secretName);
return Convert.ToString(secret.Value);
}
catch(Exception ex)
{
throw ex;
}
}
}
}In the web.config, make sure to define your vault URI:
<add key="VaultURI" value="https://yourownvault.vault.azure.net/" />
Great and Nice