TLS (Transport Layer Security) is a cryptographic protocol to provide secure communications over networks. IETF (Internet Engineering Task Force) built TLS on the SSL (Secure Socket Layer) specification which is now deprecated. Over the time, IETF release TLS versions 1.0, 1.1, 1.2, and 1.3.
TLS 1.0 and 1.1 are no longer the best cryptographic protocols. They should be disabled on both client side (browser) and server side (IIS server). I have recently came across an issue where Qualys SSL Labs tool reported that TLS 1.0 and 1.1 are active for a domain even though we disabled these protocols in IIS server.
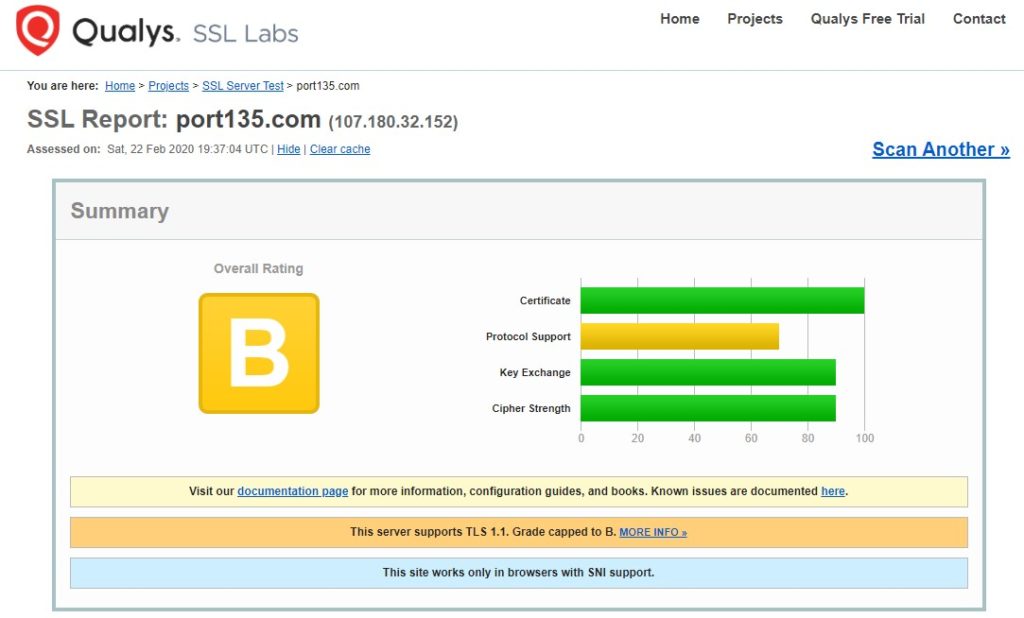
Before starting any troubleshooting about this issue, let’s first make sure that old TLS versions are actually disabled.
How to disable TLS 1.0 and 1.1 in IIS server?
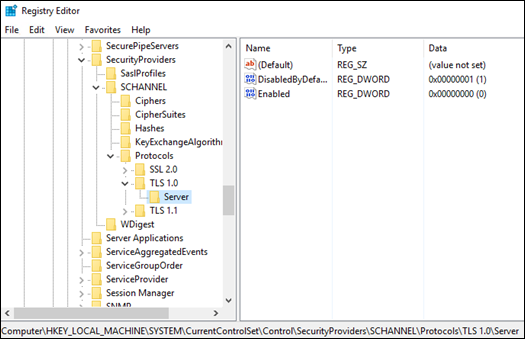
- In Registry Editor, go to the following path:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols - If they don’t exist, create
TLS 1.0andTLS 1.1keys. Under those keys, create another key,Server - In the each Server key, create
DisabledByDefaultentry (DWORD) and set it to1 - Additionally, create
Enabledentry and set it to0 - Restart the server
More details about disabled SSL and TLS versions: Transport Layer Security (TLS) registry settings
Force the browser to use specific TLS versions
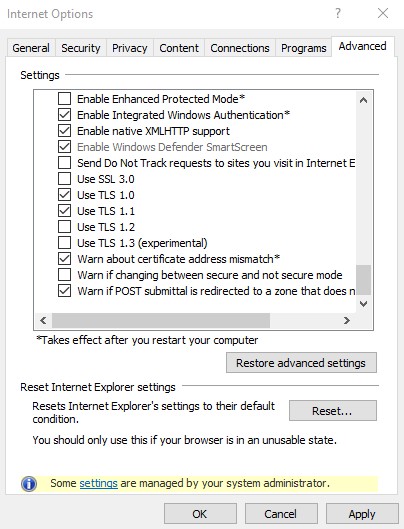
After adding the registry entries above, follow the steps below to force Internet Explorer using TLS 1.0 and 1.1.
- In Internet Explorer, go to “Internet Options”
- Select “Advanced” tab
- Scroll down in the “Settings” list. Uncheck “Use TLS 1.2”
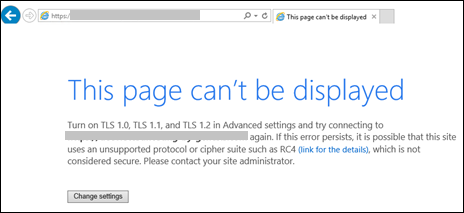
It’s time to test your application. If TLS 1.0 and 1.1 are no longer active, you should see the error below:
This page can’t be displayed
Turn on TLS 1.0, TLS 1.1, and TLS 1.2 in Advanced settings and try connecting again. If this error persists, it is possible that this site uses an unsupported protocol or chiper suite such as RC4, which is not considered secure. Please contact your site administrator
TLS 1.0 and 1.1 are still active?
If your application is still accessible through TLS 1.0 or 1.1 even though you disabled these protocols in registry, follow the steps below.
- Make sure that FIPS is disabled. Check my another post out to see how to check the FIPS value: Schannel – The internal error state is 10013
- If you have a load balancer, proxy, firewall or any other network device in front of your IIS server, try to bypass these devices by directly accessing the application. In the issue I worked on, DPI (Deep Packet Inspection) was enabled in SonicWall firewall which caused serving TLS 1.0 and 1.1 requests unwillingly
After finding out the root cause and disabling older TLS versions for good, you may come across to TLS error code 20. Here are the step-by-step instructions to solve this issue: TLS fatal error code 20. The Windows SChannel error state is 960

2 thoughts on “Security Scan (Qualys SSL Labs) shows TLS 1.0 and 1.1 are enabled”