U.S. government has a standard to define minimum security requirements for cryptographic modules used in applications. The name of this standard is FIPS (Federal Information Processing Standard). The newest version of the standard is currently FIPS 140-2.
I have recently received a question: Are these libraries FIPS compliant/certified (Microsoft.Owin, Interop.olelib, SignalR, EntityFramework, Microsoft.AspNetCore)? My answer is below.
FIPS 140-2 certified (compliant, validated) Microsoft libraries
Microsoft validates only the cryptographic modules for FIPS 140-2 instead of validating libraries or high-level applications. This is because a certain library or application can be used in both FIPS-approved and non-FIPS approved way depending on which security methods are called in the code.
Therefore, it is not possible to say if the listed Microsoft libraries are FIPS compliant or not. The question here is that if the developers of the application used these libraries in FIPS-approved way.
In order to make sure an application uses only FIPS-approved security methods:
- Only FIPS validated cryptographic modules should be installed (List of modules)
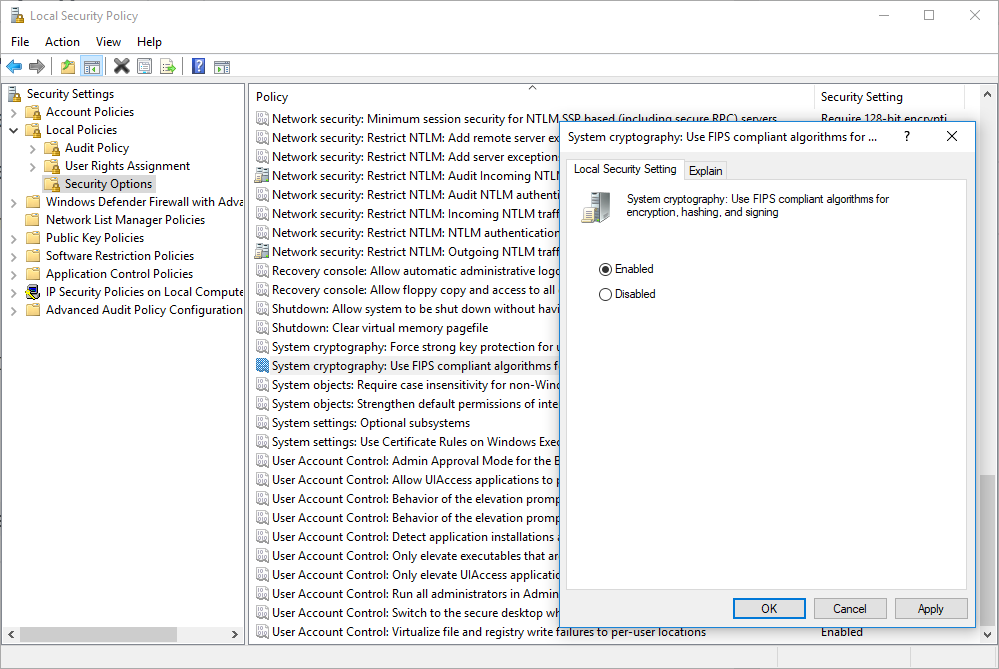
- The FIPS Security Policy Flag should be set to “Enabled” in Windows
- Developers should check this flag in code and enforce the policy to use only FIPS-validated cryptographic modules
Once these requirements are met, the .NET Framework application will allow only the implementations that are validated to FIPS 140-2. If code references non-validated implementations, the application will throw InvalidOperationException.
How to make sure that libraries use only validated modules when FIPS mode is on?
If the FIPS Security Policy Flag is enabled (FIPS mode is on), the application will use only the validated cryptography modules. This is by-design and it is not feasible to confirm what modules exactly are referred in each DLL. You can simply rely on this by-design behavior.
If a developer tries to use a non-validated module explicitly (hard-coded function call to a non-validated module), .NET will throw InvalidOperationException error if the FIPS mode is on.
Effects of Setting FIPS Local/Group Security Policy Flag:
Source
Any Microsoft .NET Framework applications, such as Microsoft ASP.NET or Windows Communication Foundation (WCF), only allow algorithm implementations that are validated to FIPS 140, meaning only classes that end in “CryptoServiceProvider” or “Cng” can be used. Any attempt to create an instance of other cryptographic algorithm classes or create instances that use non-allowed algorithms will cause an InvalidOperationException exception.
Turning on or off the FIPS mode may be the solution for certain issues. Here is an Schannel error that has relation to the FIPS setting: Schannel – The internal error state is 10013 (Solved)

1 thought on “FIPS 140-2 Validation and Compliance for Microsoft libraries (DLLs)”