While working on installation of Microsoft Identity Manager in IIS server, I came across this error message:
Runtime Error
Description: An exception occured while processing your request. Additionally, another exception occured while executing the custom error page for the first exception. The request has been terminated.
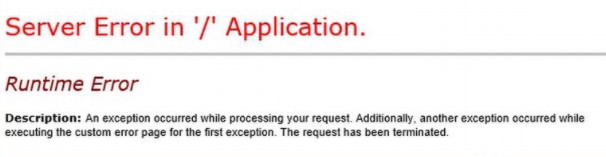
The error message doesn’t tell anything about the root cause. Therefore, I checked the Event Viewer logs.
Event ID 1310
Exception type: ConfigurationErrorsException
Exception message: An error occurred creating the configuration section handler for customAuthentication: Exception has been thrown by the target of an invocation. (C:\Program Files\Microsoft Forefront Identity Manager\2010\Certificate Management\web\web.config line 582)
This implementation is not part of the Windows Platform FIPS validated cryptographic algorithms at System.Security.Cryptography.RijndaelManaged..ctor()
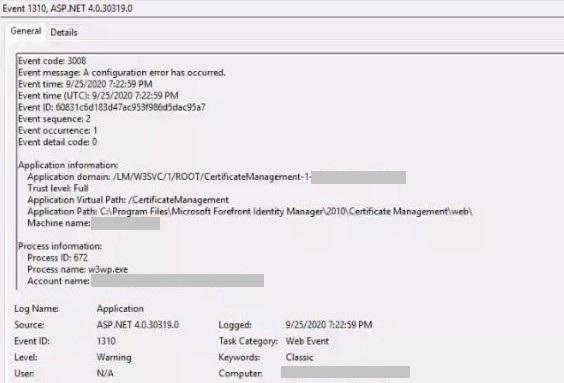
The first part of the warning (An error occurred creating the configuration section handler) is a red herring. There was nothing wrong with the web.config file.
The second part of the warning (This implementation is not part of the Windows Platform FIPS validated cryptographic algorithms) revealed the root cause.
Solution for “This implementation is not part of the Windows Platform FIPS validated cryptographic algorithms” error
The issue was the incompatibility of the FIPS with the Certificate Management of the Identity Manager. After disabling FIPS, the site started working.
I explained how to configure FIPS in this post: Schannel – The internal error state is 10013. Here are the steps:
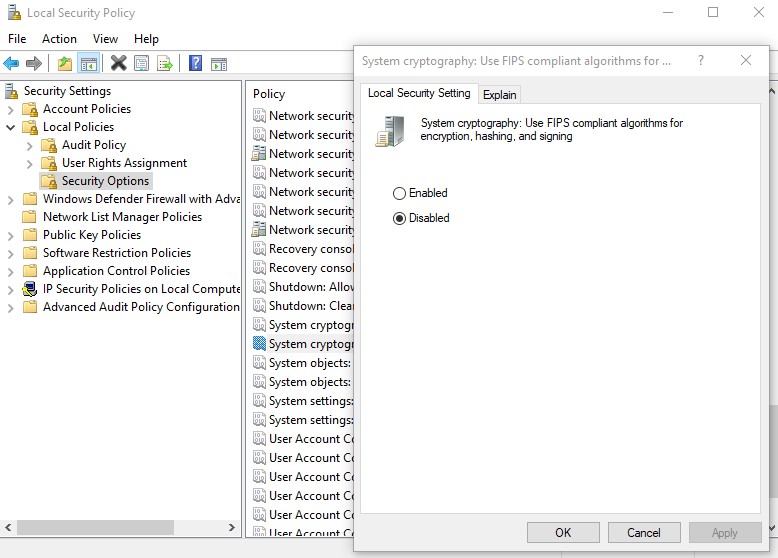
- Go to “Control Panel“.
- Click “Administrative Tools“
- Double click “Local Security Policy“
- In “Local Security Settings“, expand “Local Policies“. Then click “Security Options“
- Double click “System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing”
- Select “Disabled“
- Click “OK“
- Restart the server
You can run “gpupdate /force” instead of restarting but I saw changes not going into effect in some cases so I recommend restarting the server.
After the restart, check the FIPS setting and make sure it wasn’t enabled back. If it was, you will need to request Security team to create exception for this server.
Instructions I followed for installation of Identity Manager to IIS server is here.
For more information about FIPS validation check my other post out: FIPS 140-2 Validation and Compliance for Microsoft libraries (DLLs)
