IIS comes with a default website as well as default error pages. In order to help developers and server administrators troubleshoot issues, these error pages may provide detailed information about the application and server. Therefore, some penetration testing tools may flag this situation as a vulnerability.
Here is the vulnerability a security scan tool flagged because the default error page was in use:
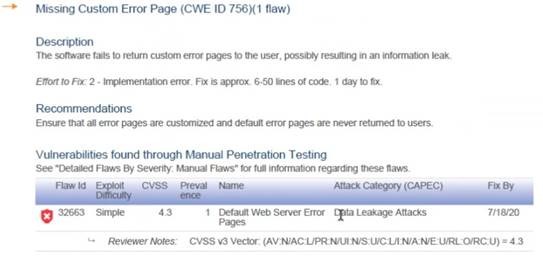
Missing Custom Error Page (CWE ID 756)
The software fails to return custom error pages to the user, possibly resulting in an information leak.
Ensure that all error pages are customized and default error pages are returned to users.
More information about this type of weakness is here.
Solution for Missing Custom Error Page (CWE ID 756) vulnerability
Unless you enable detailed error pages for remote requests, I wouldn’t classify this situation as a vulnerability. However, if you want your users to see more meaningful error pages and you want to have a clean security scan report, you can create custom error pages.
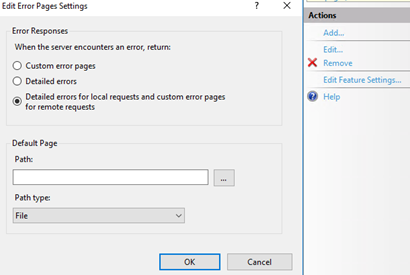
In the case I worked on, the pentest tool brought up this report for a folder that doesn’t have a default index page. For this situation, there are a few easy workarounds:
- Add an index.html file to the folder and move index.html to the top in Default Document section of that folder in IIS Manager. This should prevent that URL to be flagged again
- Customize IIS defaullt page for 403 error (C:\inetpub\custerr\en-US\403.html). Pentest tool is likely to mark the URL pass if that page is customized
- Enforce custom error pages in web.config
Here are solutions for several other vulnerabilities I have come across in the past:
- Disable HTTP OPTIONS Method for IIS
- Remove the default page or stop/disable the IIS server
- Slow HTTP POST vulnerability Denial of Service (DoS) attack
- Host Header Attack and Vulnerability
- Slow response times and Timer_MinBytesPerSecond in HTTP.SYS logs
- Do not disclose private IP addresses and routing information to unauthorized parties
- HTTP TRACK and TRACE verbs
- HTTP/2 SETTINGS frame bug and related registry keys
- Secure cookie flag
- XSS (Cross Site Scripting) attacks in ASP.NET applications
