You may run into “Schannel – The internal error state is 10013” message if your website fails establishing TLS connection. That is to say, here is the error message you will see in Event Viewer:
Info – Schannel – Creating an SSL server credential.
Error – Schannel – A fatal error occurred while creating an SSL client credential. The internal error state is 10013
This error is logged when there are Schannel Security Service Provider (SSP) related issues. For example, web server might be trying to use an encryption algorithm or protocol that were actually disabled.
Similarly, incompatible machine keys or machine keys with insufficient file permissions may be other possible reasons of “The internal error state is 10013” error message.
Looking for a way to fix “SChannel error state is 960”? Check this post out.
How to solve “The internal error state is 10013” issue
Follow the steps below to solve this issue. If no more 10013 errors logged after performing these instructions, please make sure that all other applications and services you use in the server are working as expected.
Correct file permissions
Correct the permissions on the c:\ProgramData\Microsoft\Crypto\RSA\MachineKeys folder:
- Everyone Access: Special Applies to: This folder only
- Network Service Access: Read & Execute Applies to: This folder, subfolders and files
- Administrators Access: Full Control Applies to: This folder, subfolder and files
- System Access: Full control Applies to: This folder, subfolder and Files
- IUSR Access: Full Control Applies to: This folder, subfolder and files

After these changes, restart the server. The 10013 errors should dissappear. However, If you still see “Schannel 10013” errors in EventViewer, try the next solution (keep the changes you made in Step 1).
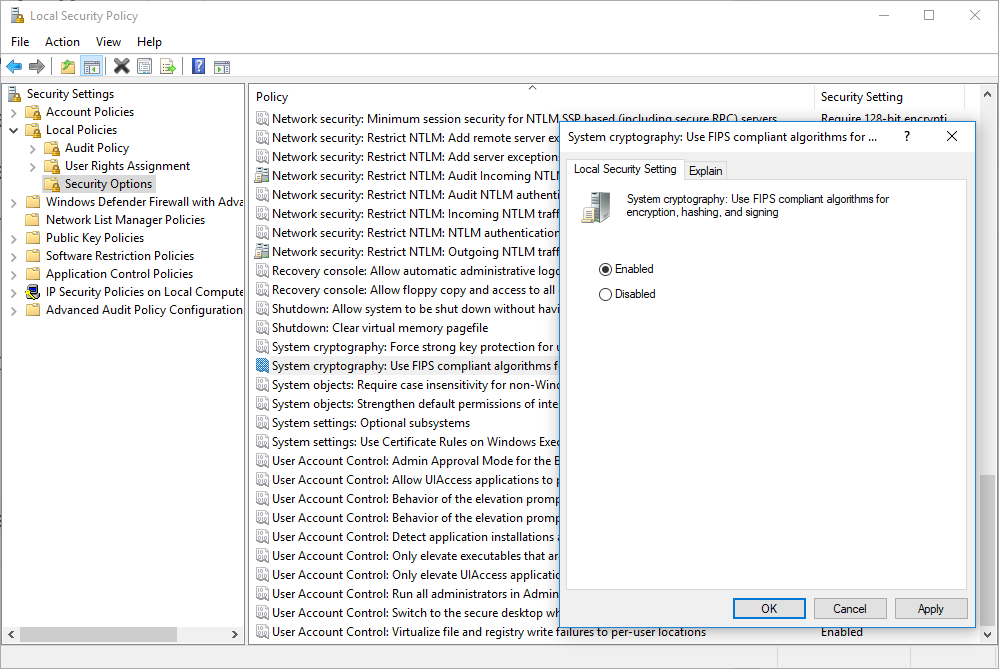
Enable “FIPS compliant algorithms for encryption”
Important!!! Even if this setting solves the problem for your application, it may break other applications in the same server! Please test all applications after performing these steps. Enabling “FIPS compliant algorithms” means disabling SSL 2.0/3.0 and forcing TLS 1.0+. A good reading about this setting: Why You Shouldn’t Enable “FIPS-compliant” Encryption on Windows
- Go to “Control Panel“.
- Click “Administrative Tools“
- Double click “Local Security Policy“
- In “Local Security Settings“, expand “Local Policies“. Then click “Security Options“
- Double click “System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing”
- Select “Enabled“
- Click “OK“
- Run
gpupdate /force
In conclusion, the two methods above should solve the issue. As mentioned above, please make sure all services work expected after these changes.

This is not a great solution. The first allows anyone on the machine to read the private keys of any machine certificates. The second enables FIPS compliant algorithms which are not recommended for general use. They have known compatibility issues.
Elizabeth, this is applied to the folder, not the keys. The Everyone –> Special permissions are actually the default. You can see the files exist, but have no rights to the items in the folder.
I’m having same issue here; AND you left out a HUGE detail!
WHICH ‘special’ access? Special is not ‘one thing.’ you have to “Show Advanced” under Security tab on the folder, and THEN tell us (the readers), EXACTLY “which” Special Access settings need to be made for the “Everyone group;” i.e., which check-boxes are checked in advanced security. “Special Access” can mean, literally, a MILLION combinations of those check-boxes! Okay, not a million, but you get the point.
“Everyone Access: Special Applies to: This folder only” <– DETAILS, please.
Everyone Special is as follows for that folder:
In Advanced permissions,
Boxes 3-7 all are checked in left column
Boxes 1, 2 & 5 are checked in right column.
Currently on one of my servers, Administrators also have Full permissions but it is for “This folder only”, fyi.
And those are the ONLY 2 permissions.
I would also question giving IUSR ‘FULL’ control all the way down the chain – is that documented by Microsoft somewhere? Thanks!
This doesn’t work for me at all and I’m getting the event log crammed with so many of these stinking error I can see NO OTHER items in the event log. I have nearly 700 of these every second.
When I go to set security permissions, they “are not enumerated”; can’t change even with Administrator privilege’s. I stopped at trying to change ownership.
In 2021 NO ONE should be enabling FIPS algorithms. By ENABLING FIPS you are installing OLD, and cryptographically INSECURE protocols like DES, and TRIPLE DES. At this point in time ( Nov 2021 ), its best practice to enable TLS v1.3 using ( 2 ) Micro$oft Registry Edits, and then use iisCRYPTO tool from NARTAC to set the rest. Use PCI v3.x “template” to be most secure if you don’t know what your doing inside of the tool, but also note that if you use that template, you will still have weaknesses. Nartac is releasing an updated tool that handles TLS v1.3 soon.
In my experience, the SCHANNEL 10013 error is caused by an app ( like MS Office 2019 ), wanting to communicate over a DISABLED TLS v1.0 or 1.1 connection. You can let it auth to the internet to activate over v1.1, and then turn v1.1 off with iisCrypto afterwards…..it won’t need it again even after Sysprepping. I don’t believe that there’s any stopping this error unless you can hunt down the app causing it, and somehow make that app stop trying to use a Disabled protocol.
I FIXED SCHANNEL 10013 ERROR ! ! ! (in Windows 10)
1) Set folder permissions as prescribed – Rebooted
2) Disabled FIPS compliant algorithms – in Local Policy
3a) Turned on “Use TLS 1.3 (experimental)” – in Internet Options
3b) Turned on “Use SSL 3.0” – in Internet Options
4a) Loaded Template PCI v3.x – in ISSCrypto
4a) Added “SSL 3.0” in Both Server & Client – in ISSCrypto
5) Cleared “System” Event Log and REBOOTED
ALL SCHANNEL 10013 ERRORS ARE GONE!
I’ve been working this problem for about 4 months.
Thanks for all the tips and procedures! -neal
OMG… thank you. THANK YOU!
Your tutorial worked and lots of different ones didn’t.
I still have this error Microsoft-Windows-Security-SPP ID 16385 , 0x80041315